Auditing Kubernetes with rbac-police
Kubernetes pods can be abused to take over the entire Kubernetes cluster. rbac-police shows you which.
Kubernetes is a container orchestrator, providing a raft of supporting services which ensure that application containers can run with all the essential bits they need such as networking, configuration and storage. Applications are called pods and they can also speak to the Kubernetes API, allowing them to fetch useful information back from Kubernetes.
Pods can be given additional Kubernetes permissions which allow them to interact with Kubernetes without having to pass in passwords or tokens manually. This is used a lot! Pods can create other pods, or watch for new pods and create auxiliary services such as load balancers in the cloud.
With some of these permissions, a Pod has enough permissions to accumulate more until it has full control over the Kubernetes cluster or even the cloud service account hosting it. With full cluster control, attackers can schedule their own workloads (cryptominers), steal data from other services or cause havoc.
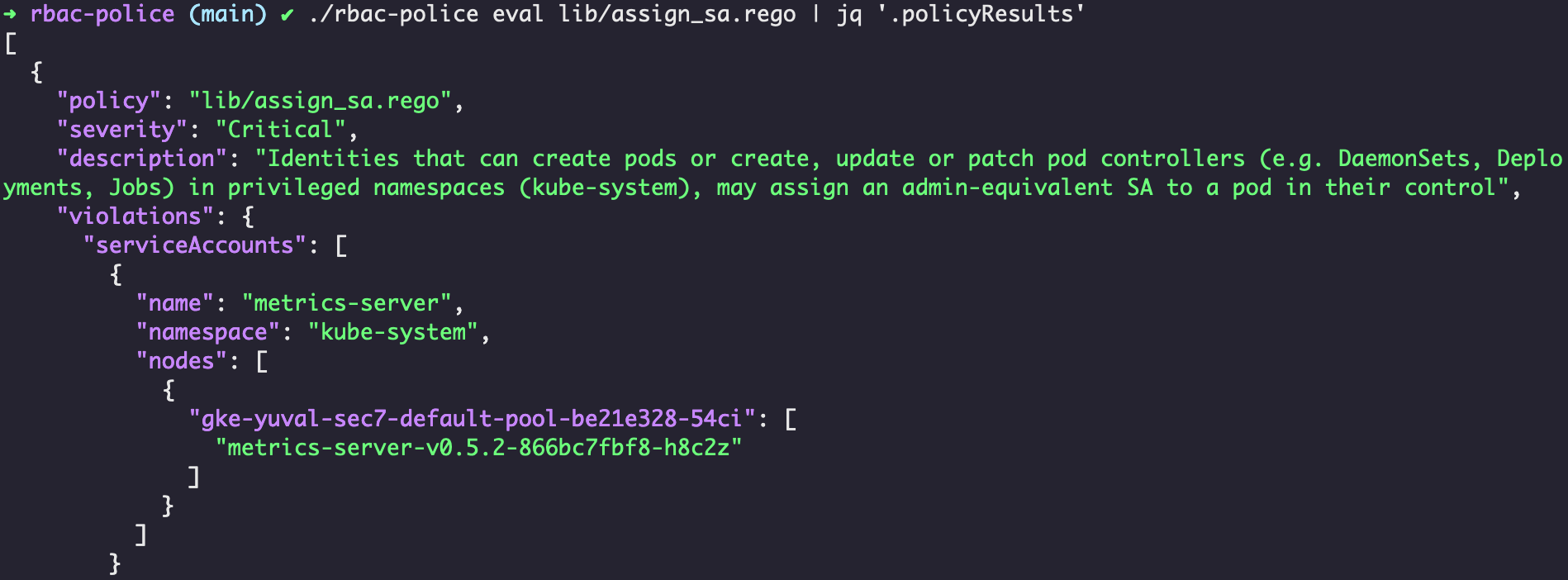
Palo Alto did some great research into this attack approach, culminating in this white paper and the tool rbac-police.
We recently used rbac-police as part of a wider Kubernetes security assessment for a client and found that their nginx ingress had far too many permissions which allowed for a full kubernetes takeover. This issue is particularly bad as the NGINX ingress is a web proxy, public facing and receiving direct connections from hosts over the internet. A vulnerability within NGINX could have led to full cluster compromise.
When we dug deeper into this, we found that the nginx ingress had been deployed from the official ingress helm chart which gave permission to get secrets in all namespaces, including very sensitive secrets in control namespace.
- apiGroups:
- ""
resources:
- secrets
verbs:
- get
- list
- watch
Switching to the Kubernetes community maintained ingress helm chart fixed the issue as the permissions were much tighter.
- apiGroups:
- ""
resources:
- configmaps
- endpoints
- nodes
- pods
- secrets
verbs:
- list
- watch
Kubernetes auditing is a complicated topic, but assessing the RBAC assignments within the cluster is a critical part of a full holistic audit.
We provide Kubernetes-specific security reviews and penetration testing. Read more here
