dnsReaper gets ProjectDiscovery Chaos and SecurityTrails support

dnsReaper is designed to check your own domains, but now we’ve added Project Discovery and SecurityTrails support too!
By adding direct integration with Project Discovery and SecurityTrails, dnsReaper moves into the purple space and becomes much more powerful for penetration testers and bug bounty hunters.
So what are these two new integrations we are so excited about?
Project Discovery CHAOS
Project Discovery is an open-source software company with some absolutely fantastic tools, including the hugely popular Subfinder tool.
Subfinder scans online sources to passively identify subdomains for a domain. Let’s break that down…
If we scan actively, we run the risk of the target noticing our actions. Maybe we download a webpage, do a port scan or request millions of subdomain resolutions.
To scan passively means we use alternate sources not related directly to the target, so they cannot possibly notice our activity. Subfinder is a passive tool, it looks for potential subdomains in certificate transparency lists or through search engines.
Subfinder is used by penetration testers and bug bounty hunters, so Project Discovery built an online database of its findings called CHAOS. Rather than scanning every time, you can ask CHAOS for those subdomains. … and that’s exactly what we now do in dnsReaper!
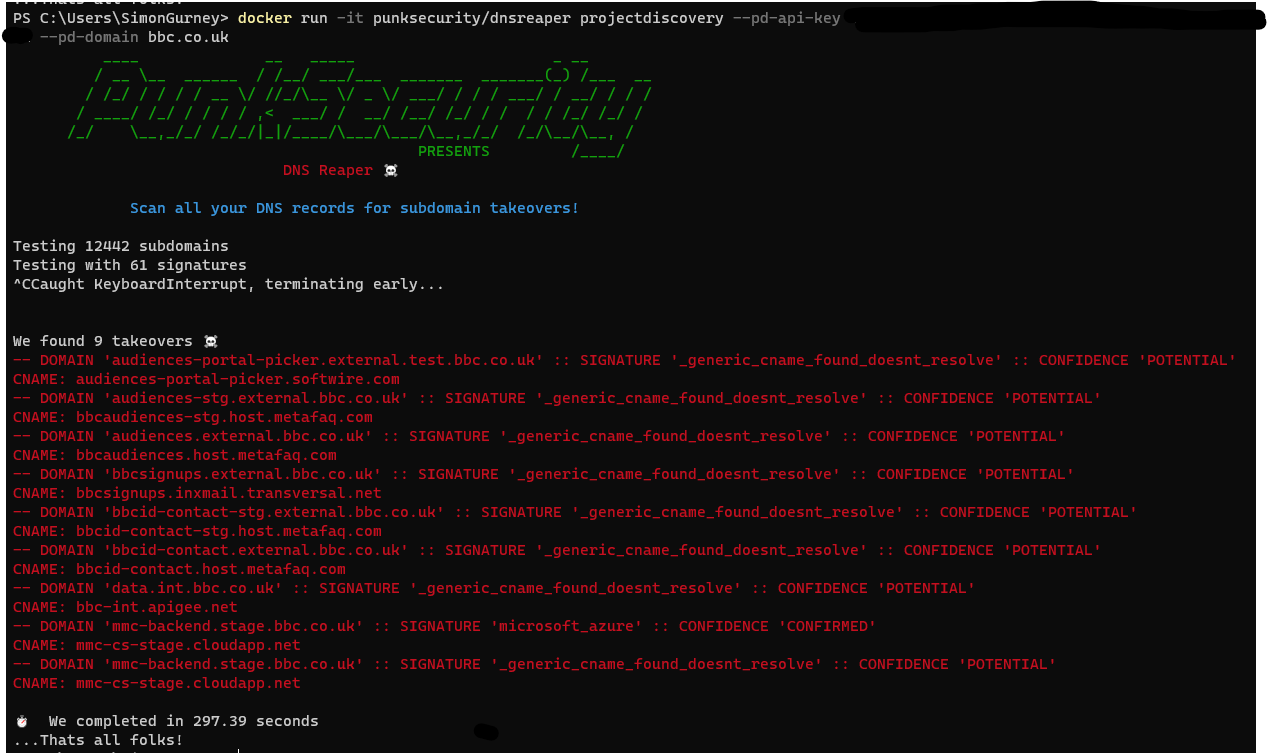
Running a scan against a domain with project discovery is so easy, you just need to grab an API key from their Google form and then give it to dnsReaper.
docker run -it punksecurity/dnsreaper projectdiscovery --pd-api-key <key> --pd-domain <domain> --parallelism 100
In this command, we use the projectdiscovery provider, and then give it an API key and target domain. We also increase the parallelism. This allows us to scan faster. When we are scanning 100% legitimate records, which is the default case for most providers, we choke the number of parallel resolutions down because you will end up being rate-limited by your DNS provider. With this projectdiscovery provider, you will likely find that half the subdomains don’t exist anymore, so you get DNS timeouts which slows down the scanning engine anyway.
SecurityTrails
SecurityTrails is an attack surface management SaaS platform which monitors your DNS records and hosts. It’s a great tool but it also provides a similar API to CHAOS (although with a quite limited free request quota).
By integrating it into dnsReaper, you can query subdomains passively from their database before automatically feeding the results through the dnsReaper subdomain takeover engine.
python main.py securitytrails --st-api-key <key> --st-domains <domain> --parallelism 100
In this command, we use the securitytrails provider and feed it an API key and comma-separated list of domains. As with our projectdiscovery provider, we also increase our parallelism to account for the number of slow querying false subdomains.
So what!?
This is HUGE news for us.
We built dnsReaper as a blue team tool. It connects directly to your DNS provider (AWS, Google Cloud, Azure, GoDaddy, Cloudflare etc) and downloads your exact DNS record. No brute-forcing, no false positives. We then check them for misconfigurations that could be used by an attacker to hijack those domains.
What we found is that penetration testers and bug bounty hunters loved dnsReaper and started feeding it a huge wordlist of subdomains to try and attack. Wordlists coming from Subfinder or other tools.
This latest change means we can provide this functionality out of the box and take some complexity away!
dnsReaper is no longer a blue team tool, but a pedigree purple!
If you want the latest version of dnsReaper, pull the latest docker image or clone the latest tag from Github
docker pull punksecurity/dnsreaper
OR
git clone https://github.com/punk-security/dnsReaper.git #or git pull if you already cloned
git checkout 1.9.3
