Defending from bots with Cloudflare
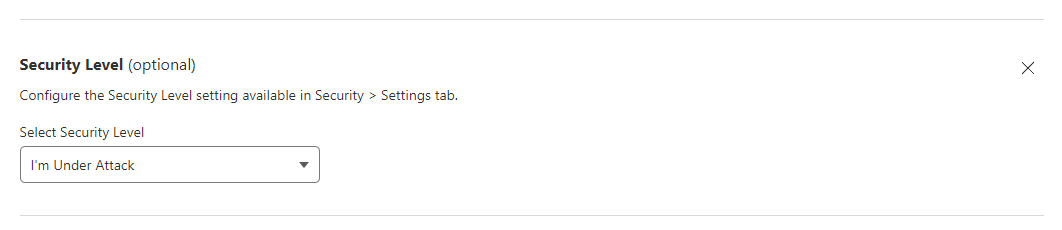
We use Cloudflare to protect our CTF from spam bots, VPNs and hackers.
Punk Security is a Cloudflare partner, so it’s the obvious choice for protecting our CTF platform.
Cloudflare proxies all traffic to our CTFd instances and Apache Guacamole game interface, providing out-of-the-box protection against DDoS attacks and known bad actors. This is a fantastic service, it’s really simple to configure and is such a low cost that it is our default recommendation for any public-facing web infrastructure.
What it doesn’t do is stop bots from creating users on our CTF platform. This is a challenge faced by a lot of platforms, with twitter being the most publicised recently.
In our case, we have no social interactions on our CTF platform, and all of our challenges have unique flags. This means we don’t need to concern ourselves with bots from automatically playing our ctf, but it would still be really annoying if we wake up to 1000 new user accounts on the platform.
To protect from this with Cloudflare is trivial! We add a simple rule to protect the registration and login pages of our site. Cloudflare will then place its protection service in front of those two pages.
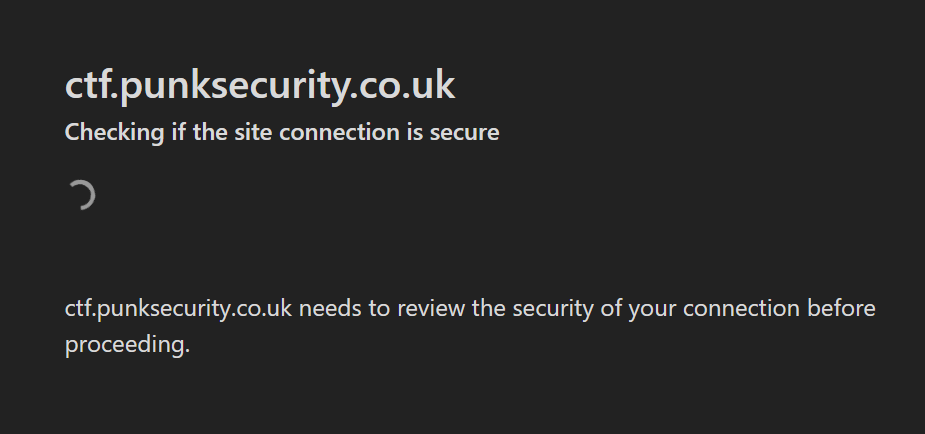
For most users, they see a Cloudflare splash page, but if you fail the automatic Captcha process then you will have to complete a Captcha form.
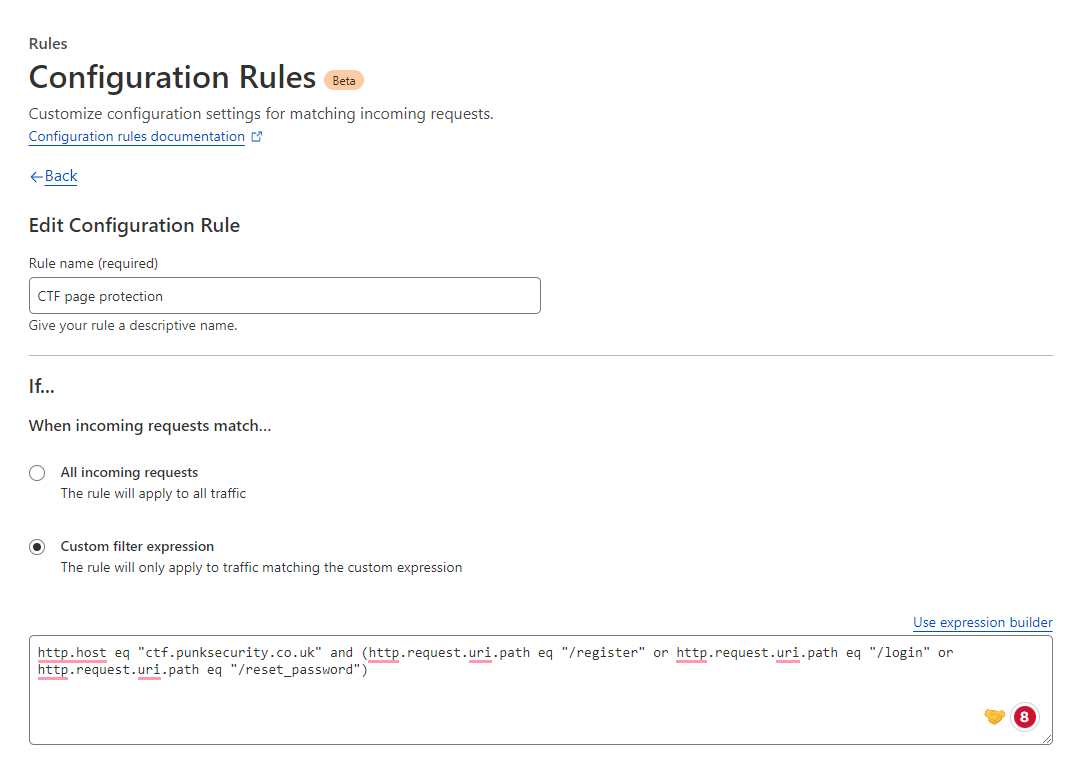
The actual configuration is shown below. It looks a little complex, but actually we are just checking that:
- The request is to our ctf platform
- The request is either for a login, register or a password reset request.
There are instances where this would not work, and we’ve helped customers with some very difficult DDoS and bot protection challenges, but occasionally it can be this simple.
